You may be aware or unaware of the news of the current “wildfire” raging in the tech scene about the data breach and hack of thousands of MS Exchange Servers worldwide that has got governments and organizations scrambling and fumbling. The hack exposed some vulnerabilities and risks in Microsoft Exchange Email Servers 2010, 2013, 2016, or 2019. Basically, a bug/backdoor was noticed that exposes all your organization Emails to the public! This has been big news as over 800k MS Exchange servers exist outside there and over 60k of them were recorded to have been exposed in the US alone! This was so “epic” in not so a good way, that it has got a place on Wikipedia Page here: Wikipedia: 2021 Microsft Exchange data breach: https://en.wikipedia.org/wiki/2021_Microsoft_Exchange_Server_data_breach
The attack was discovered after attackers were discovered downloading all emails belonging to specific users on separate corporate Exchange servers. The reading from Volexity, the initial company that documented the incident makes for quite a read:
The attacker was using the vulnerability to steal the full contents of several user mailboxes. This vulnerability is remotely exploitable and does not require authentication of any kind, nor does it require any special knowledge or access to a target environment. The attacker only needs to know the server running Exchange and the account from which they want to extract e-mail.
As The Verge reported, about the doubling numbers from 30k to 60k, I could not but be afraid and sorry for the IT Admins who world over who were running MS Exchange. Executives in this organization were likely yelling and screaming at/to and subjecting them to the endless “why did we not…” yells. Add to the widely held misconception, among some of the highly regulated organizations and enterprises is that “having our data here, where we can see it makes it’s safe “. So they end up missing and exposing their businesses to these threats and attacks. Because let us face it, “the only people who know how to properly secure and administer an MS Exchanger Server are Microsft themselves.” Not my words, but the words of Alex Stamos, former Yahoo and Facebook Chief Security Officer (CSO)
@alexstamos I remember years ago when you gave a presenation at WhiteHat, you actually said that the only company qualified to run Exchange was Microsoft. And here we are.
— Jeremiah Grossman (@jeremiahg) March 8, 2021
Snapshot of the Impact
Breaking into Exchange Server offered the attackers access to any sensitive communications that a business conducted by email. It also allowed hackers to exploit the vulnerabilities to spy on a wide range of targets, affecting an estimated 250,000 servers. The severity of the hacks is felt throughout the organization and business spectrum through lost productivity, the loss in person-hours and service delivery to your customers, stolen IPs, and sometimes lost real Money when Business Email Compromise and Spoofing are put to use to the compromised emails. Some organizations reported attackers sending convincing emails to contacts in a social engineering attack that encouraged recipients to click on a link. Norway’s parliament reported being a victim of the hack, stating that “data has been extracted.” And the European Banking Authority also admitted that it was also a victim of the attack!
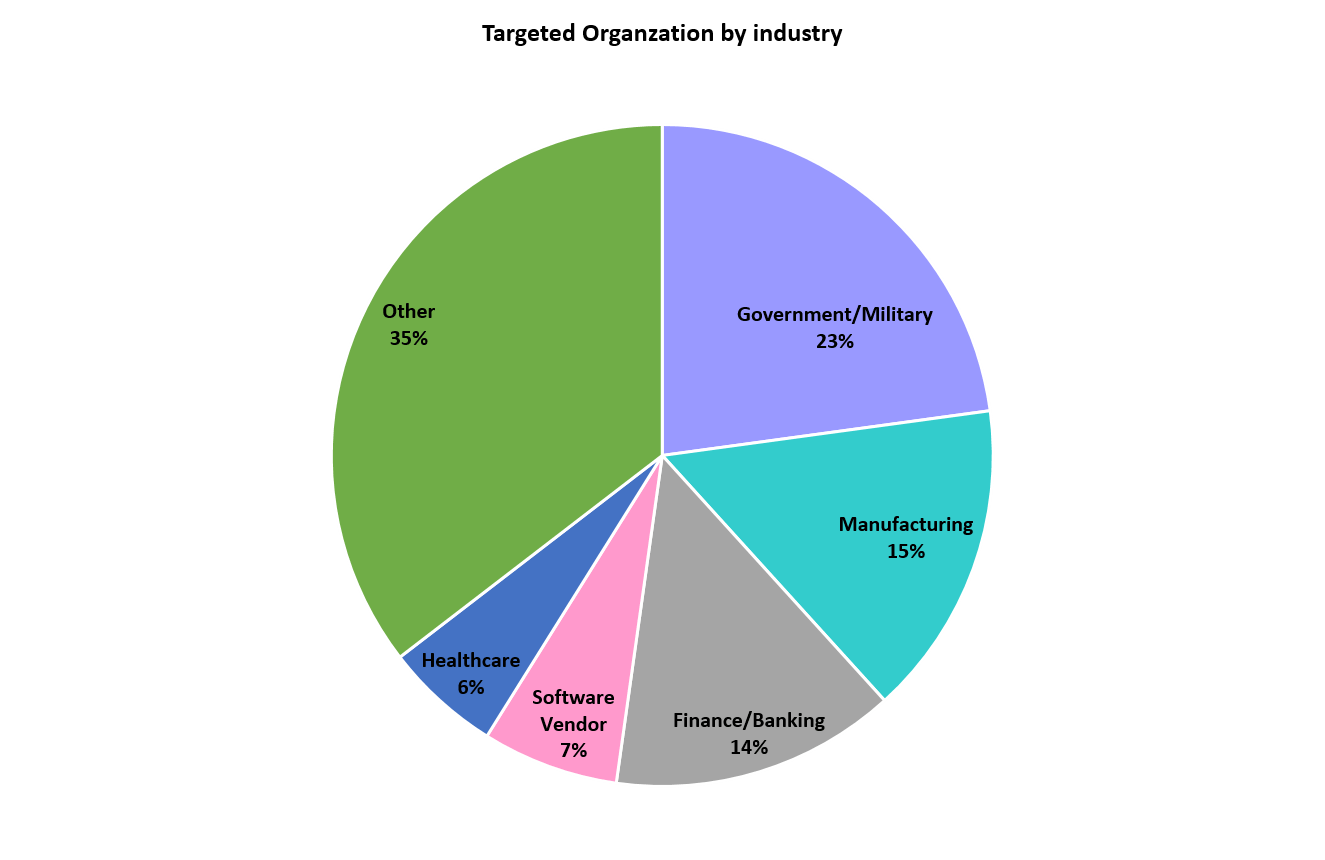
No one was immune and as Checkpoint Research broke it down, here are the most impacted industries:
Most targeted industry sector has been Government/Military (23% of all exploit attempts), followed by Manufacturing (15%), Banking & Financial Services (14%), Software vendors (7%) and Healthcare (6%).
Solution: Patch and Update? Or is it?
Authorities in the US, EU, and UK rushed to advise all organizations running MS Exchange (2010, 2013, 2016, or 2019) to apply the patches as soon as possible and to create offline backups of their Exchange servers. But I like what the US National Security Council said: “Patching and mitigation is not remediation if the servers have already been compromised. It is essential that any organization with a vulnerable server take immediate measures to determine if they were already targeted.”
Patching and mitigation is not remediation if the servers have already been compromised. It is essential that any organization with a vulnerable server take immediate measures to determine if they were already targeted. https://t.co/HYKF2lA7sn
— National Security Council (@WHNSC) March 6, 2021
In short, if you run an MS Exchange, consider/assume that you have been hacked. Even if you patched/applied the updates to fix the servers. You need to start making plans to mitigate for the future/ not known attacks yet. And if you are among the ones saying “it was just an MS Exchange issue, us we are on xyz/abc server, so we are safe! “. Please, be aware that if Microsoft, with all its mighty $$$ muscle and might got compromised, who/how far do you think the people at “xyz/abc server” would fair on?
If your organization is affected /impacted or unsure, perhaps this may be a good time to explore the potential of moving your organization’s email and communication systems to the cloud. And what better and safe and secure cloud to consider than Google Cloud Workspace. The same system that runs and protects Google systems such as Gmail, is provided for organizations that want to move to the cloud.