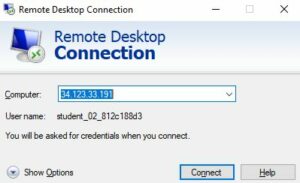
Remote desktop is a valuable tool, especially for sysadmins. It has also been the source of many cyber-attacks, which have cost organizations millions of dollars. Ensuring RDP is secure and properly configured is essential to network security.
Remote Desktop Protocol is developed by Microsoft and it is a proprietary protocol that provides a user with a graphical interface to connect another computer over a network connection. It runs on the client-server-based architecture. On the server computer, RDP server software should be installed and on the client-side, the user must employ the RDP client software for this purpose.
Port 3389 of your Remote Desktop Protocol (RDP) is enabled and allows connections from any IP around the world, by default on Google Cloud Platform. It has many benefits but can also be a cause of a threat and a high-security risk. If some attacker performs a brute force attack on your RDP and can remotely access your device(s), then all your sensitive data can get compromised. How can we deal with this now? We have two options: either restrict RDP access over your VMs or select a range of IPs or specific IPs to access your VMs.
Restricting your Remote Desktop Protocol (RDP) to access VMs isn’t challenging but it requires some understanding of GCP VPC(Virtual Private Connection). We can ensure this by using firewall rules. While deploying a VM, it expects a firewall rule to be assigned. You need to create firewall rules beforehand and directly employ the same rules to the new compute instance deployments.
How to secure your RDP
- The set password which is complicated and powerful in nature consists of uppercase, Lowercase, Numeric- Password complexity may seem like a gimme, but this is one of the simplest ways to increase the security of your remote desktop connections. While the common password complexity recommendations used to be eight characters long with a mixture of uppercase, lowercase, numbers, and symbols, nowadays, that’s not enough. Newer computers can brute force a password with these complexity requirements in just a couple of hours. Some security specialists now recommend passwords have a minimum length of 12 characters with a mixture of uppercase, lowercase, numbers, and symbols. Others suggest even longer passwords. As you increase the password’s length, the time it takes to brute force the password goes up exponentially.
- Set number of user restriction on RDP
- Regular update to new version of the software and download software and applications from secure websites only- The advantage of RDP being a Microsoft owned solution is the constant stream of updates. Microsoft is swift to patch vulnerabilities. Make sure you stay vigilant in keeping your systems patched and up to date. Just remember to review updates before applying them. Microsoft has been known to push updates that can break features or introduce new bugs.
- Provide multilayer authentication ex. Email, contact no. – MFA(Multi-Factor Authentication) is highly regarded as an effective method of securing resources, including RDP connections. While phishing scams and brute force attacks have proven to be effective ways of obtaining user credentials, without the second form of authentication, attackers will still be unable to access user accounts.
- Secure your port
- Buy RDP from secure sites-avoid grace period time settings of 120 days elapsing on your instance while on other schedules and activities and getting locked out of your RDP connections sessions
- Limit Login Attempts-Limiting the number of login attempts before locking out an account is another way to deter brute force attacks. Brute force attacks can attempt thousands of passwords in seconds. However, if an account is locked out after three failed attempts, then the brute force attack is stopped in its tracks. While this may sound like the perfect solution to brute force attacks, it does have drawbacks. If an attacker wanted to, and if they had access to usernames, they could lock out hundreds or thousands of users from their accounts in a matter of seconds. Attackers could also use this method to harvest usernames because only valid usernames would become locked out of a system.
Isn’t this just “Cloud and Clear”, talk to our team of GCP Cloud Certified Experts for more insights on RDP at https://pawait.africa/contact-us/