How to enhance your security posture in your enterprise cloud using Investigation Tool: Case for Google Workspace
Episode 6: Security Center: Investigation Tool
Security investigation tool is used to identify, triage, and take action on security and privacy issues in a given domain in Google Workspace. For instance the tool can be used to:
- Access device log data to get a clear view of the devices and applications being used to access your data.
- Access Gmail log data to find and erase malicious emails, mark emails as spam or phishing, or send emails to users’ inboxes.
- View search results that list suspended users.
- Access data about devices.
- Access Drive log data to investigate file sharing in your organization, investigate the creation and deletion of documents, investigate who accessed documents, and more.
- Access data about Gmail messages, including email content.
How to Search and investigate user log events
Investigation tool can be used to search and investigate user log events, and take action based on the results of investigations done. For instance, you can do the following:
- Identify and investigate attempts to hijack user accounts in your organization.
- Monitor which 2SV methods users in your organization are using.
- Learn more about failed login attempts by users in your organization.
- Restore or suspend users.
To search and investigate user log events, go to Google Admin console (at admin.google.com):
- In the admin console, go to Reporting -> Audit and Investigation -> User log events
- Choose User log events as the data source for your search.
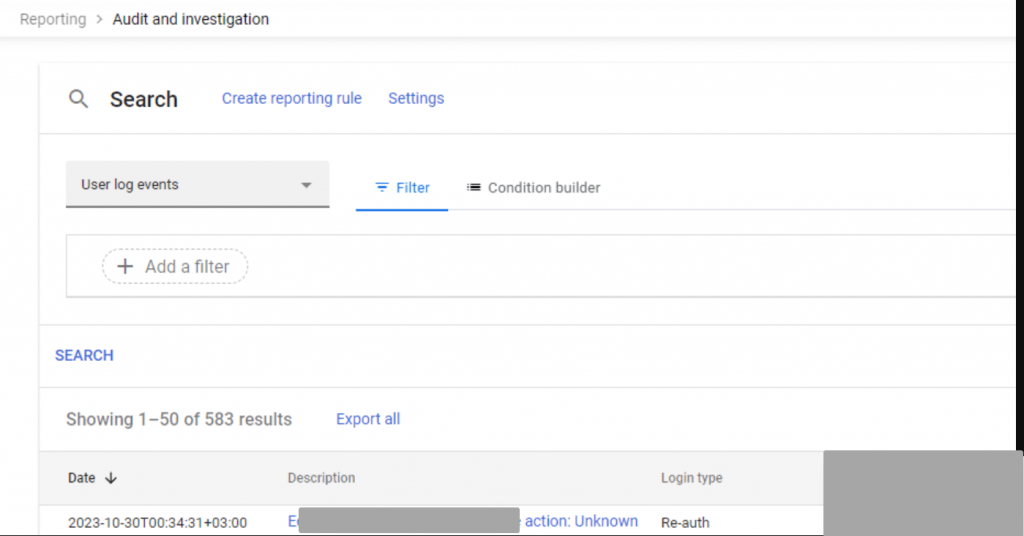
- Click condition builder then Add Condition. You can include one or more conditions in your search.
- Click Search. The search results are displayed at the bottom of the page.
- From the search results page, select one or multiple users. Then, from the Actions drop-down menu, click Restore user or Suspend user.
Stay tuned for our episodes, we shall:
- Google EMM: Remote Wipe Devices: Windows, Android and iPhone