Passkeys-Access Google Workspace Account without a Password
What are Passkeys?
Passkeys are a safer and easier alternative to passwords. It’s a digital credential that ties to a user account, website, or application. Passkeys built on FIDO standards (Fast Identity Online), enable all browsers to adopt them easily. Its main aim is to replace legacy authentication mechanisms such as passwords.
How do Passkeys work?
When a user wants to sign in to a service that uses passkeys, their browser or operating system will help them select the right passkey to use. To make sure only the rightful owner can use a passkey, the system will ask them to unlock their device. More so, users can sign in to apps and websites with either a biometric sensor (fingerprint or facial recognition), PIN or pattern. More so, this frees them from remembering and managing passwords.
Users can select an account to sign in with and not need to type the username. Users can seamlessly switch to a new device and immediately use it without needing to re-enroll. On Android, the Google Password Manager stores passkeys and synchronizes them between the user’s Android devices signed into the same Google Account.
Even more, they are available on phones and used when logging into a laptop, even if the Google Workspace passkeys isn’t synchronized to a laptop provided the phone is near the laptop and the user approves the sign-in on the phone.
What makes Passkeys very secure?
Passkeys use Public Key Cryptography for potential data breaches such as phishing attacks, brute force attacks, session hijacking & credential stuffing attacks.When a user creates a passkey in a site or application, it generates a public-private key pair on the user’s device. Notably, the site stores the public key, but this alone is not useful to an attacker. An attacker can’t derive the user’s private key from the data stored on the server, which helps complete authentication.
Advantages of Passkeys
- Security: It provides a layer of security by verifying the identity of users before granting access.
- User-Friendly: Designed to be user-friendly, allowing individuals to choose and remember passkeys that are meaningful to them.
- Confidentiality: They are confidential and known only to the authorized user.
- Multi-Factor Authentication (MFA): They are part of multi-factor authentication methods, combining two or more types of authentication factors (e.g., password and biometric scan).
- Convenient: Instead of remembering passwords for different sites, users can use passkeys.
- Google Lockout: Locks out an account from illegal access in case of a Brute Force attack.
- They are resistant to phishing because they are not sent over the network.
Enable Passkeys in Google Workspace: Getting Started
Google Workspace passkeys are currently in open beta within all Google Workspace editions. To get started, Admins should access their organization’s Google Admin Console and navigate to the menu under Security > Authentication > Passwordless.
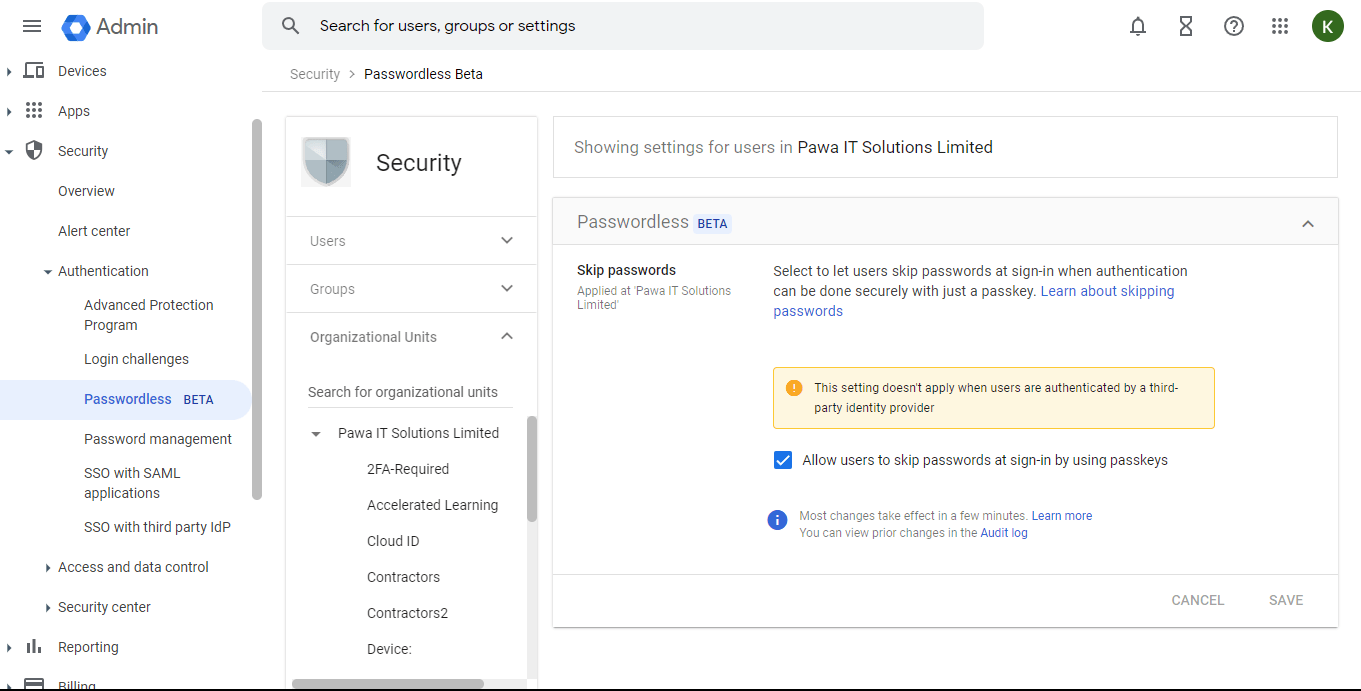
Note that by default, the setting “Allow users to skip passwords at sign-in” is off.
An Admin can decide to choose to turn the feature on for the entire organization by selecting the top organizational unit or turn on the feature for a specific group by selecting a sub-organizational unit. More so, it can override the inherited setting from the parent-organizational unit.
Setting up Google Workspace Passkeys
- Users can navigate to g.co/passkeys after enabling passkeys and can begin the setup process for Google Workspace passkey.
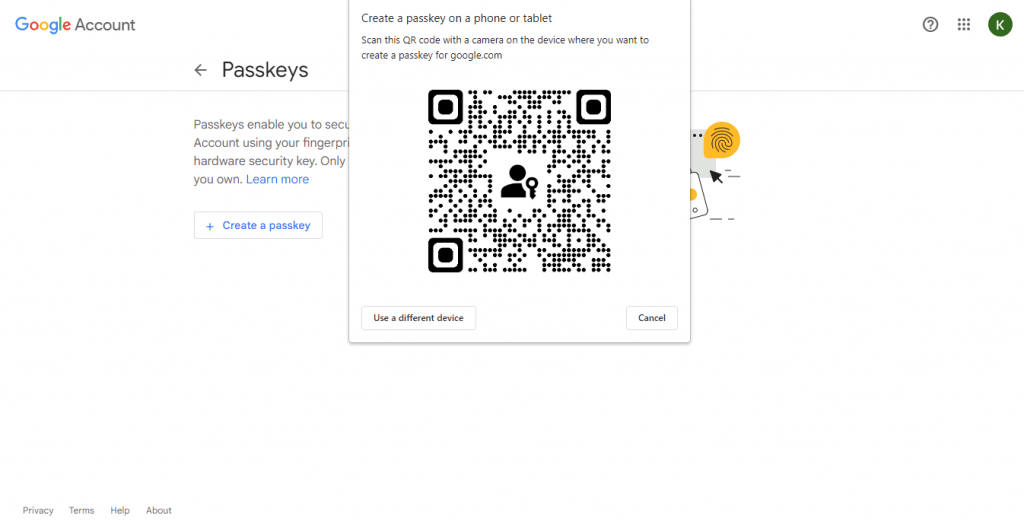
- If they have no Google Workspace passkey associated with their Google account, they can click the Create a passkey button, which will bring up a QR code for them to scan using the camera of the device where they want to create the passkey.
- The scanned QR Code (Illustration here) will then prompt the user to access a link with the format “FIDO:/35”, and ask whether they want to allow their mobile device to connect to the requesting device with the QR Code. They can also check the box “Remember this computer” if they trust the device.
- The mobile device will establish a connection to the computer and inform the user that they can either use their fingerprint, face or screen lock to verify their identity with a passkey. The user’s email, which uses the passkey, will display for confirmation.
- More so, this prompts the user to input either their fingerprint, face or PIN, depending on their preference, which will finalize their registration, with their computer verifying the success of the passkey creation.
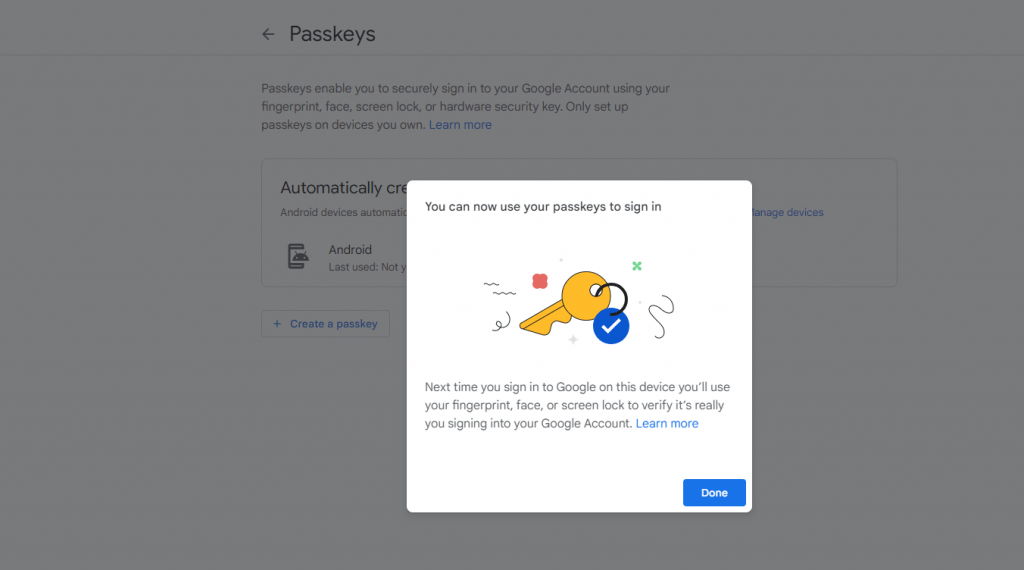
- The user can then view the passkeys created and associated with their Google account.
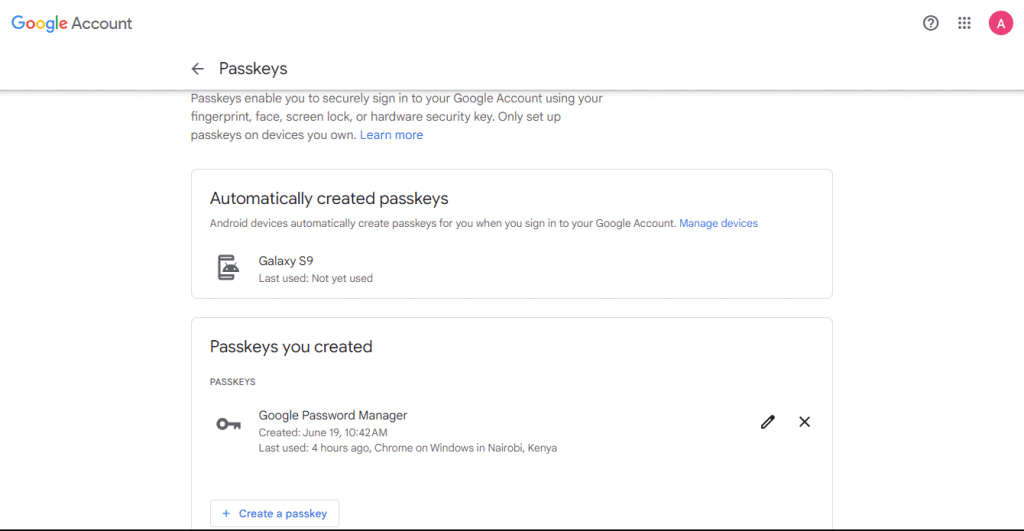
Sign-in Via Google Workspace Passkeys
- When the user accesses their account, they will see a notification guiding them on how to use their newly created passkey by clicking on “Try another way.”
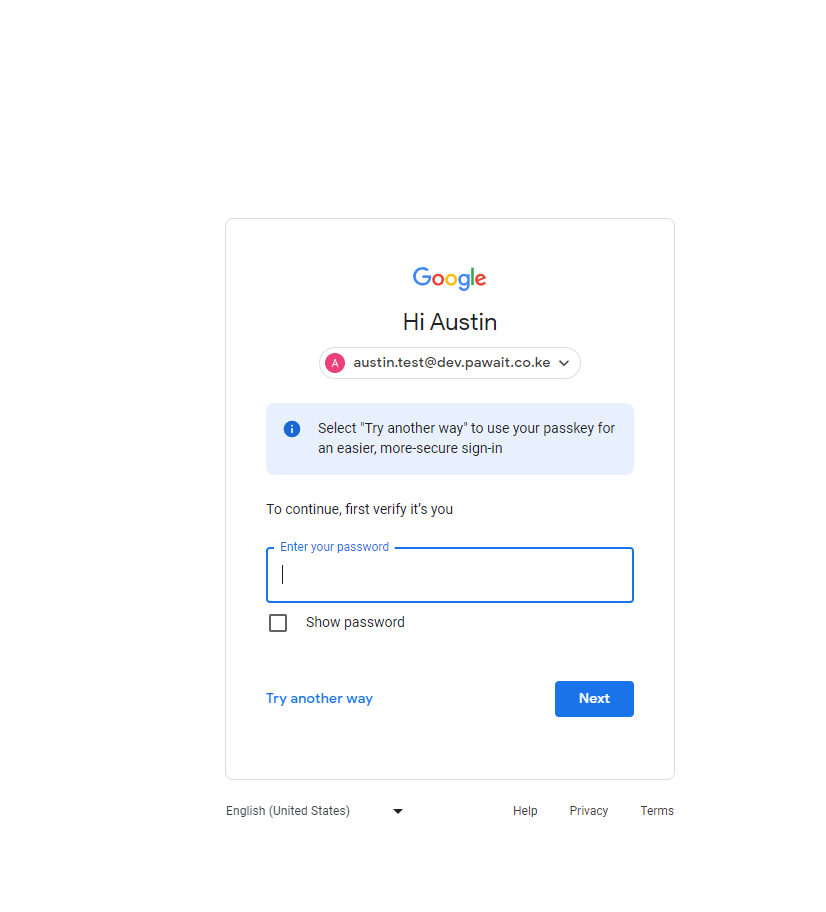
- Here, they will see the option to sign in using their Google Workspace passkey.
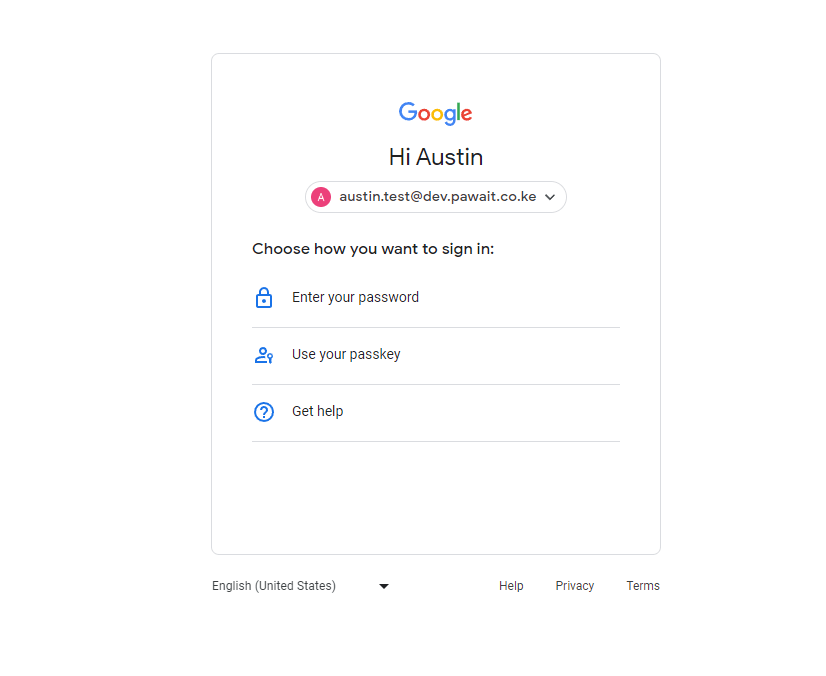
Different Signin options
- By clicking on “Use your passkey,” a popup will appear asking them if they will use the passkey generated on the most recent device or if they want to use a different device.
- A prompt will appear on the chosen device, asking the user to verify their identity on the computer. When clicked, the mobile device will attempt to connect to the laptop and then ask for either the fingerprint, face scan, or PIN, depending on what the user chose during setup.
- When their identity is successfully verified, the user will receive a notification that “Sign-in succeeded” on their mobile device, and they will be able to access their Google account on the computer Google Workspace Passkeys.
Check what you need to create a passkey
You can develop passkeys on these devices:
- A laptop or desktop that runs at least Windows 10, macOS Ventura, or ChromeOS 109
- A mobile device that runs at least iOS 16 or Android 9
- A hardware security key that supports the FIDO2 protocol
Your computer or mobile device will also need a supported browser like:
- Chrome 109 or up
- Safari 16 or up
- Edge 109 or up
To create and use a passkey, your device must have the following enabled:
- Screen lock
- Bluetooth
If you want to use a passkey on a phone to sign in to another computer
Tip: To ensure the best passkeys experience, we recommend you update to the latest available releases for your operating system. Depending on your operating system and browser, you may not be able to create or use passkeys while in private browsing mode like incognito or other equivalents.
Additional resources